Have you ever walked into a store (Or been binge-scrolling on Amazon, no judgement) and seen a tool that you didn’t know you needed, but absolutely can’t live without? Or maybe walked in looking for the bare-bones version of a tape measure, but walked out with the ultra-pro-max version the product? Whether this was a nail gun, a mixer, a toaster, or even a phone, it’s so common for us to focus in on getting the “best of the best” without really considering our needs. We may have the best nail gun in the east, but the daunting 100 page instruction manual may mean we only utilize 10% of the potential it has. An old saying rings true here, “Potential energy does not equate to useable energy”. For many of us in the cybersecurity space we see the shiniest, newest tools and get them “running”, but never care to read that 100 page instruction manual. Just like our nail gun, these tools sit idly by, only being utilized to 10% of their capacity. This month, we are going to focus on what just the right amount of security tool might look like, and learn how maximizing the security tools we have can surpass buying the best of the best but leaving them on the shelf.

To start out, we need to assess where we are with our security toolset. Smaller organizations are less likely to fall victim to this, as budgets are tight and many spends – especially on risk aversion – are kept minimized. However, for midsize to large organizations it can be easy for tools to be bought and forgot. Security teams have needs that fit within the yearly budget but fail to be assessed after the fact. To determine if you are over-tooled for security, consider the spend on security tools versus the needs for the business. The recommendations below operate based on my experience that the overwhelming majority of security incidents start on the endpoint, and that identities are the second reason trialing behind. The references to tooling will be done in Microsoft offering terms, as they offer the most solutions in one place.
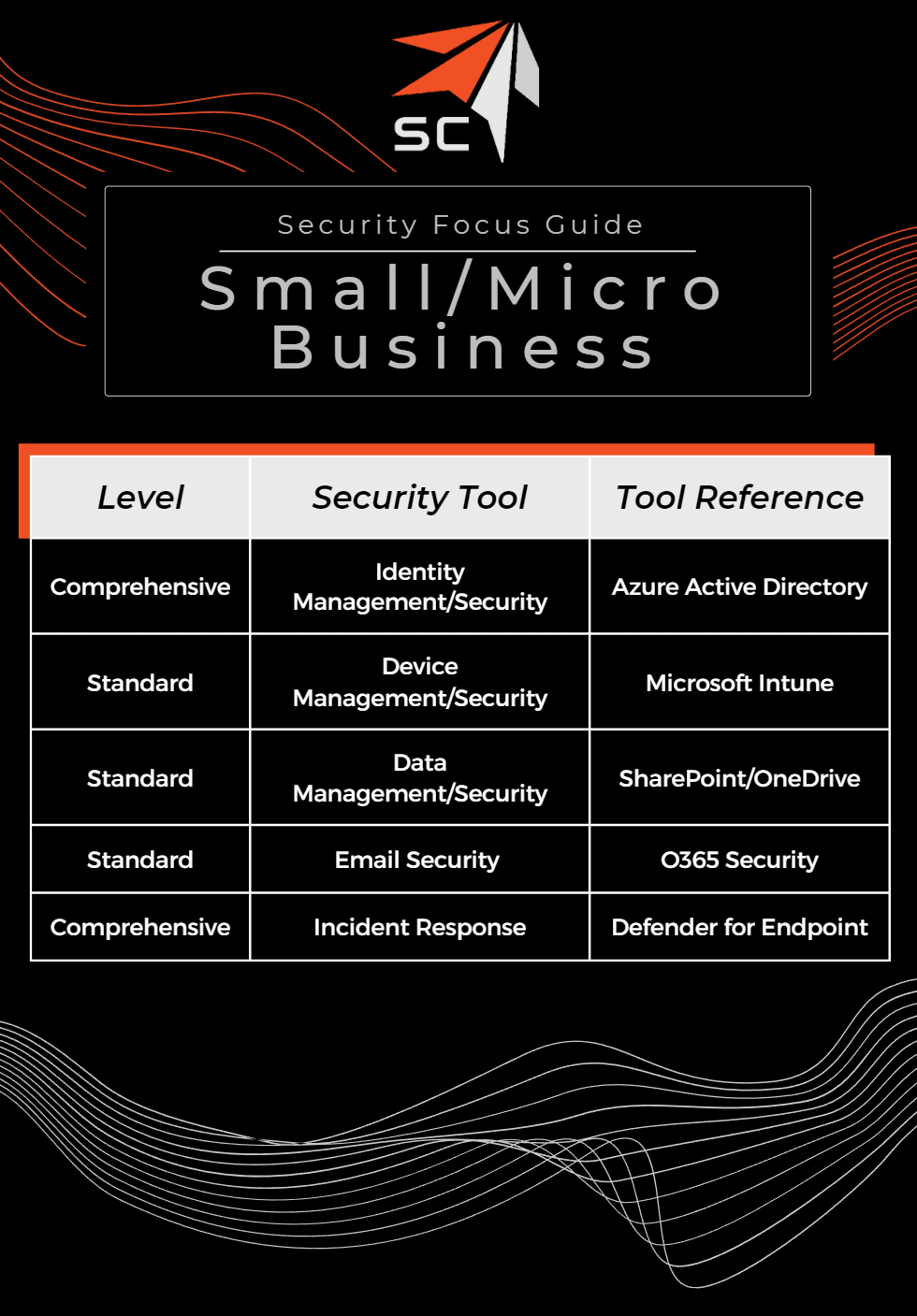


In all reality, many organizations are not over-tooled, but rather under-utilizing the tools they have. Even if your organization has the right level of security for the job, there is still a high probability that what you are paying for is not being utilized to the fullest. Many organizations take deep consideration into the type and level of controls they employ but leave operating the system to bean afterthought. A common example of this is buying a suite of tools from a vendor– Microsoft E3 for example – which includes a whole host of advanced functionality for a base price. While you may know that there is advanced functionality included, can you describe what the included controls do and how to leverage them effectively? The questions below can serve as a jumping off point to determine if you have the security tools in place but may not be leveraging all they have to offer. If you weren’t able to answer more than half of the questions above, it might be a good idea to take a critical look at how the security system is functioning outside of the billing invoice that pays for the service each month. Critical systems may be in place, but without the proper monitoring and attention they require, it is difficult to provide effective security. Even if you are working with a low budget, fully managing and monitoring a small set of security controls is more effective than buying the best but neglecting the alerts they create.

We all can fall victim to buying more tool than we need, or buying a tool that we put on the shelf. As security-conscious business owners, though, we have to be aware of our tendencies to do this and keep a keen eye to ensure we don’t fall into the traps they can present. While leaving a nail gun on the shelf might not be the end of the world, neglecting the security tools which are in place to protect our business and customers can have much larger implications. Ensuring that our security tools are sized to our needs and operating to their full capacity is one of the best decisions an organization can make, so if you haven’t already, go dust off those security tools currently in place and put them to work.